|
|
Introduction Implementing Other Uses Parts Example Background
For each Event Handler function with digital Signature, a hidden field will be added to the corresponding HTML form on the Document Template. This hidden field is used at run-time to store the signature belonging to the event. The Digital Signature part of the HTML form in the Document Template looks like this:
<INPUT TYPE="HIDDEN" NAME="WSYD_SIGN" VALUE="/(WSYD_SIGN)/(CANCEL)">
Note that the VALUE attribute consists of two replacement markers. The first replacement marker is the field used to store the signature, while the second replacement marker is used to store the event identifier.
When the HTML page is generated, the values of the hidden form fields are known and the Digital Signature is generated and included in each HTML form:
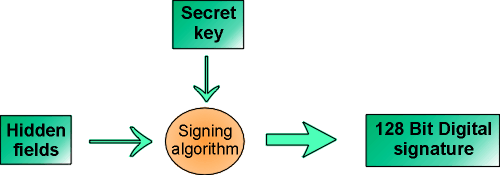
For each form on the HTML page, a Digital Signature is generated. In addition to the hidden fields themselves, a secret key (signature key) is used as input to the sign algorithm.
By default, all the hidden fields of an HTML form are included as input to the sign algorithm. It is possible though, to deselect individual hidden fields to be included as input to the algorithm.
The signing algorithm in Websydian is based on a secret key unknown to the web user. In Websydian, the Group model name of the CA Plex model is used as the default key if no other value is assigned to the key field. In this way, the same default 'secret' key will be used for all signatures generated by the application.
It is strongly recommended that functionality is specified to implement a more dynamic key generation. New keys could be defined for:
The Digital signing is performed with the "Message Digest 2" (MD2) algorithm giving a 128 bit sign. So, using the Digital sign functionality with a key kept secret for the web user, Websydian guarantees a MD2-level of security.
In the iSeries variant of Websydian, the maximum length of the resulting string used as input for the Digital Signature algorithm is 256 characters. The total length of the resulting string is calculated by:
| Result string total length | = | Length of hidden field values + 2 * secret key length + overhead |
The overhead represents two-character separation markers between the hidden fields.
If the total length of the resulting string exceeds 256 characters, the resulting input string will be truncated and all hidden fields may not be protected against changes.
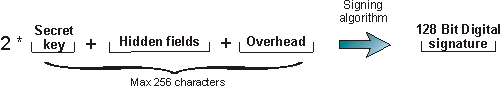
In an iSeries implementation, the resulting string of the total length of the Key + Hidden fields + Overhead must not exceed 256 characters.
In general, this is not believed to be a problem, because a solution based on the server-based Session Management concept included in the Websydian package can be used. Instead of passing a large number of hidden parameter fields through the generated HTML pages and back again by the HTML forms, an alternative solution is to pass the Session ID and then save and retrieve the needed parameter data in a table based on the web sessions.